Phishing Emails – Cautionary Tales – Part 1
9am Monday morning; “Jane” the finance director of a small roofing company turns on her PC, opens her Outlook and spends 5 minutes going through her emails.
5 minutes later her company has lost £8,500.
What happened was a failure on several levels; of procedure, of security and of system. And while the bank’s anti-fraud department was able to recover / cover the lost money, it was a mistake that nearly cost the business and took many months to recover from.
So just how did it happen?
Unfortunately; Jane’s company was something of a poster child of what not to do, their password policy was non-existent, their network security was out of date, and it was standard operating procedure for the managing director to send emails to Jane stating, ‘Please send £X to Y bank account’ without any verification.
Of course, Jane had received an email from her ‘MD’ asking her to transfer £8,500 to an anonymous bank account. The email was not from the MD but ‘spoofed’ to appear to have come from him and with the lack of proper security procedures and technical measures that was all it took.
Another day and another user; “Karen” the accounts manager at a hotel chain, receives a phone call from her contact at the business’ third party accountant firm. Her contact was concerned by the amount of money ‘Karen’ has been asking him to move to unknown accounts recently. Of course, the real Karen had no knowledge of this.
After investigation it transpires that previously; Karen had fallen foul of a phishing attack and been tricked into giving up her email credentials to an unknown party. Without two factor authentication to prevent it, the malicious party went on to read through all her emails, contact the accountant while diverting all responses to themselves and deleting any evidence, and instructing the accountant (as Karen) to transfer £36,000 to an account in the Cayman Islands. Like in Jane’s case due to this being the standard procedure the money was transferred.
Sadly, for Jane and Karen, phishing and scam emails are becoming one of the gravest concerns for moderns SMEs and yet much of the user base is ignorant of both the threat presented and the potential costs. Every day the attacks become more and more complex, increasingly realistic and harder for your average person to spot.
The above examples; while ranging from incredibly simple to technically complex, are still effective because the creator of these attacks rely on human nature. All you can do as a business is to reduce the avenues of attack and to protect the user when they make a mistake.
Once upon a time; the height of scamming was an email from a generous Nigerian Prince (Nigeria does not in-fact have a royal family) wanted to give YOU $50,000 if only you could provide them a measly $1,000 to help facilitate the transfer. Who could say no?!
Like other early scamming attempts, these emails were poorly worded, full of spelling mistakes and typos. While you do still see first generation emails like this in the wider ecosystem, modern anti-spam email filters mean the end user rarely sees them.
Of course, as the email filters and other forms of defence have evolved, so have the attacks become more complex and harder to stop. Additionally, scammers more often use phishing attacks to try and steal customer data and logon credentials rather than extract money directly.

Here we have an example of a phishing email from ‘Barclays Bank’. It is a near carbon copy of a legitimate Barclays email; and the only obvious way you can tell it is a fraud is by the hyperlink addresses.

Once the victim has clicked the link on the fraudulent email, they are often taken to a fake web page similar or identical to the real page; this is where the victim is tricked into giving up their real username and password which the malicious party with then use for their own ends.
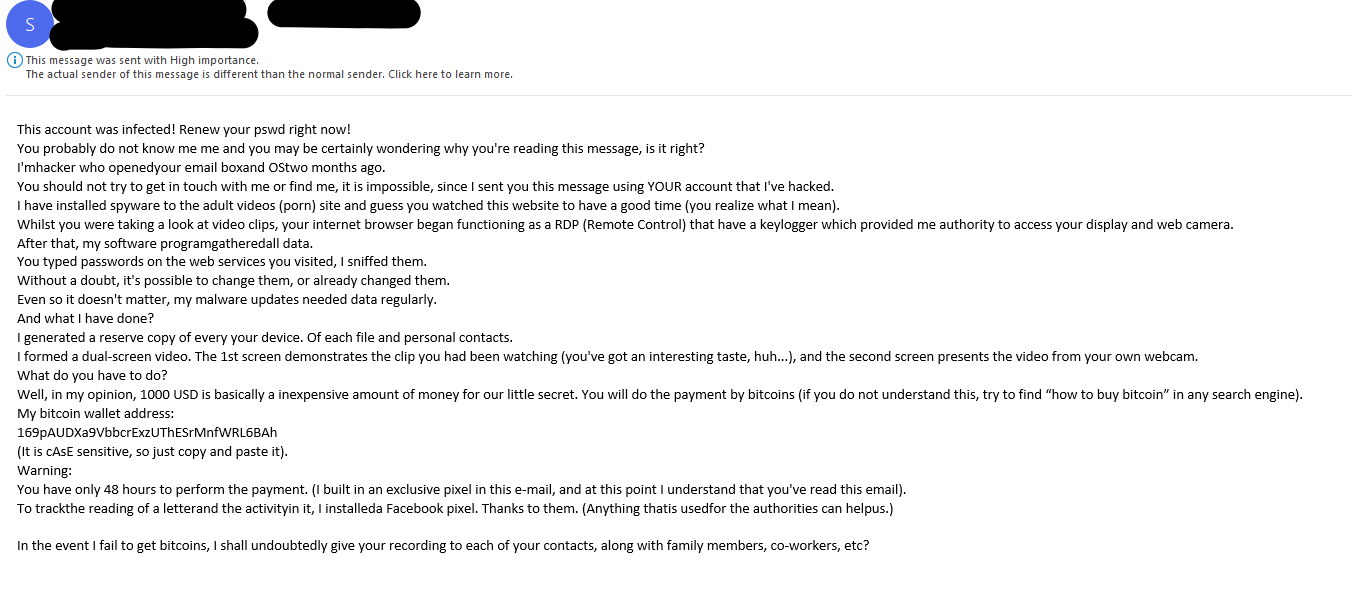
Ransom emails are very common currently; the attacker doesn’t need to do anything but spoof that the email is from the recipient, they are then relying on the user to be scared into sending the money even though there is no real threat.
Thank you for reading, I hope you found it informative/enjoyable. Next time I will be going through the ways you can secure against the threats faced by a business the Modern Workplace.
Written by Benjamin Cutler – MBM Ltd – 12/03/2019
*The above stories are based on real incidents with the affected users’ names / industry changed. Following the incidents, they approached MBM Ltd and their cases were resolved and their security improved.





